Controlling Application Permissions with Security Context Constraints SCC (OpenShift Administration
Title :
Controlling Application Permissions with Security Context Constraints SCC (OpenShift Administration)
...................................
** If new to Docker, Podman, Kubernetes and Openshift then first see -- https://www.youtube.com/playlist?list=PLnFCwVWiQz4kASpMbCXRmAu6nKtPOBE4Q
** For detail about OpenShift development --
https://www.youtube.com/playlist?list=PLnFCwVWiQz4lrK7s1S409fsfm59qdFVOX
Controlling Application Permissions with Security Context Constraints
Security Context Constraints (SCCs)
SCCs control:
• Running privileged containers.
• Requesting extra capabilities for a container
• Using host directories as volumes.
• Changing the SELinux context of a container.
• Changing the user ID.
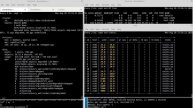
OpenShift provides eight default SCCs:
• anyuid
• hostaccess
• hostmount-anyuid
• hostnetwork
• node-exporter
• nonroot
• privileged
• restricted
Lab:
• Create service accounts and assign security context constraints (SCCs) to them.
• Assign a service account to a deployment configuration.
• Run applications that need root privileges.
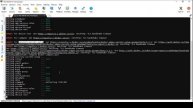
commands--
oc new-project authorization-scc
oc new-app --name gitlab --image quay.io/redhattraining/gitlab-ce:8.4.3-ce.0
Log in as the admin user
oc get pod/pod-id -o yaml | oc adm policy scc-subject-review -f -
oc create sa gitlab-sa
oc adm policy add-scc-to-user anyuid -z gitlab-sa
Log in as the developer user
oc set serviceaccount deployment/gitlab gitlab-sa
oc expose service/gitlab --port 80 --hostname gitlab.apps.ocp4.example.com
Видео Controlling Application Permissions with Security Context Constraints SCC (OpenShift Administration автора Питоновое образование
Видео Controlling Application Permissions with Security Context Constraints SCC (OpenShift Administration автора Питоновое образование
Информация
4 декабря 2023 г. 3:17:37
00:13:55
Похожие видео














![[Path of Exile] Der ULTIMATIVE Beginner Guide - Path of Building (Deutsch|2023) Ep.3](http://pic.rutubelist.ru/video/4c/5e/4c5e9f3bf27aa6526afde81859e5e155.jpg?size=s)